Configuring administrator security - PingID
Use the Administrator Security page to view or change the authentication settings for the PingOne admin console.
You can use PingID, an external identity provider (IdP), or a combination of external IdP and PingID. Some configuration might need to be done in the PingID console.
|
This topic only applies to environments that include PingID. If your environment does not include PingID, go to Configuring administrator security. |
This topic is applicable if either:
-
Your organization was created after September 16, 2024.
-
You enable enhanced security early for environments in an organization created before September 16, 2024, either from the New Security Requirement message in Administrator Security or by clicking Update Now on the Update Admin MFA Settings modal presented when you signed on to the environment.
Ping Identity will require multi-factor authentication (MFA) for all PingOne administrators as of June 1, 2025. Learn more in the PingOne administrators MFA requirement - FAQ.
You must have the Organization Admin role, Environment Admin role, or a custom role with equivalent permissions to configure Administrator Security.
Steps
-
Go to Settings > Administrator Security.
If the environment was created before September 16, 2024, and you haven’t enabled enhanced security, you must click Enable Enhanced Security on the New Security Requirement message to access Administrator Security.
-
Click the Pencil icon to change the settings.
-
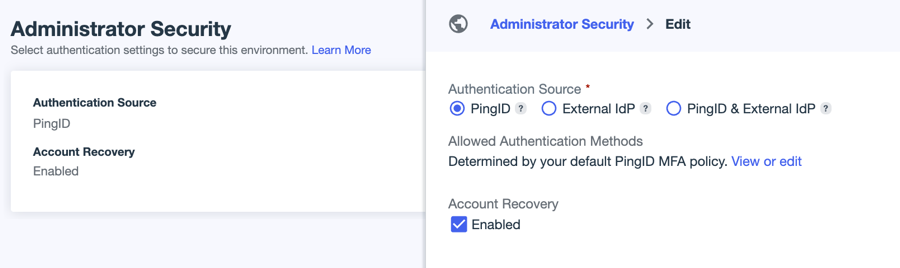
For Authentication Source, select one of the following.
Choose from:
-
PingID (default): PingID is used as the authentication source. You configure the authentication policy and set the allowed MFA methods in the PingID console. Click Configure Now to open the PingID admin portal in a separate window and configure the authentication policy.
Learn more in the Authentication Policy section of the PingID documentation.
If the environment was created after January 7, 2025, or if you are enrolled in the early access program for managing PingID in PingOne, the default MFA policy is managed from Authentication > MFA in PingOne. Learn more in (Early Access) Full management of PingID in a PingOne environment.
-
External IdP: This option is enabled only if you have configured at least one external IdP in your environment. The selected IdP is used as the authentication source for the admin console. If you select this option, ensure that your external IdP is configured to follow best practice security recommendations.
You should also test the connection to ensure that it is configured correctly. Administrators will be unable to sign on if this connection is configured incorrectly.
You can’t make changes to the IdP configuration from this page. Go to Integrations > External IdPs if you need to edit the connection. Learn more in Editing an identity provider.
-
PingID & External IdP: This option is enabled only if you have configured at least one external IdP in your environment. The selected IdP is used as the initial authentication source for the admin console. After the user authenticates through the IdP, PingID sends a secondary authentication request.
Test the connection to the IdP to ensure that it is configured correctly. If the connection to the IdP fails, as long as the administrator has a recovery account in PingOne, the administrator can sign on to PingOne directly. PingID will then prompt them for secondary authentication.
-
-
Configure the applicable settings:
Setting Description Account Recovery
PingID and PingID & External IdP only.
If selected, PingOne admins who forget their password can recover their accounts with a one-time passcode (OTP) sent to their email.
This setting applies only to the PingOne account, and not to the external IdP. Account recovery for the external IdP is managed by the provider.
Identity Provider
External IdP and PingID & External IdP only.
Select the IdP to use for authentication.
This IdP will be labeled with an Administrator IDP badge in Integrations > External IdPs. The IdP can’t be disabled or deleted while assigned in Administrator Security.
If you change the selected IdP, the settings for the new IdP are used for authentication. You should always test the connection configuration when you change this setting to ensure that administrators are able to sign on to PingOne. Learn more in Troubleshooting test connection failure.
-
Click Save.