Installing and uninstalling PingFederate
PingFederate operates as a standalone server based on Java EE application server technology. This section shows you how to properly install PingFederate.
A new installation involves:
-
Determining the deployment architecture
-
Completing the Initial Setup wizard
|
To avoid issues with browsers honoring Private Network Access security practices, you should make PingFederate accessible on a public network address if you intend to use it with applications or partners that would be considered public resources. |
Deployment architecture options
Depending on your needs and infrastructure capabilities, you can choose a standalone or proxy configuration. For information about configuring proxy settings, see Configuring incoming proxy settings and Configuring forward proxy server settings.
The following diagram illustrates a standalone PingFederate deployment in a DMZ.
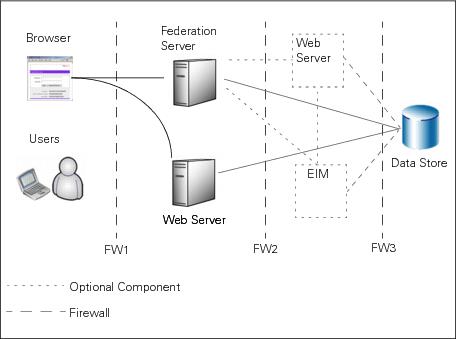
In this configuration, the users access PingFederate through a web application server, an enterprise identity management (EIM) system, or both. PingFederate then retrieves information from a datastore to use in processing the transaction.
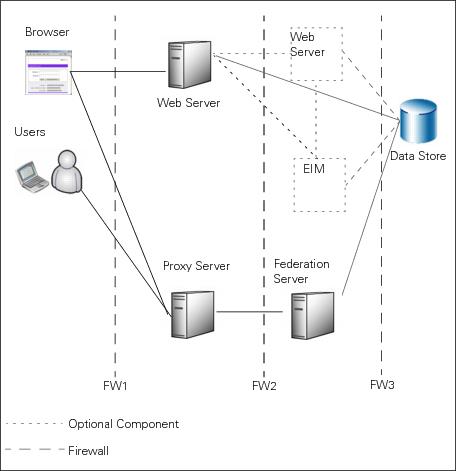
You can also deploy PingFederate with a proxy server. The following diagram depicts a proxy-server configuration in which users and web browsers access the proxy. The proxy then communicates with PingFederate to request single sign-on (SSO).